Hello Everyone .
This is October – Tuesday Microsoft Security updates:
***
in this artical I’m focuse on pathcing for Microsoft Windows Server 2016 and Exchange on prime 2016…
***This update supports daylight saving time (DST) changes in Greenland.
**This update addresses security issues for your Windows operating system and Exchange Servers.
*****Note: till now there no anyone reports any issues or bugs after installing this month patches.
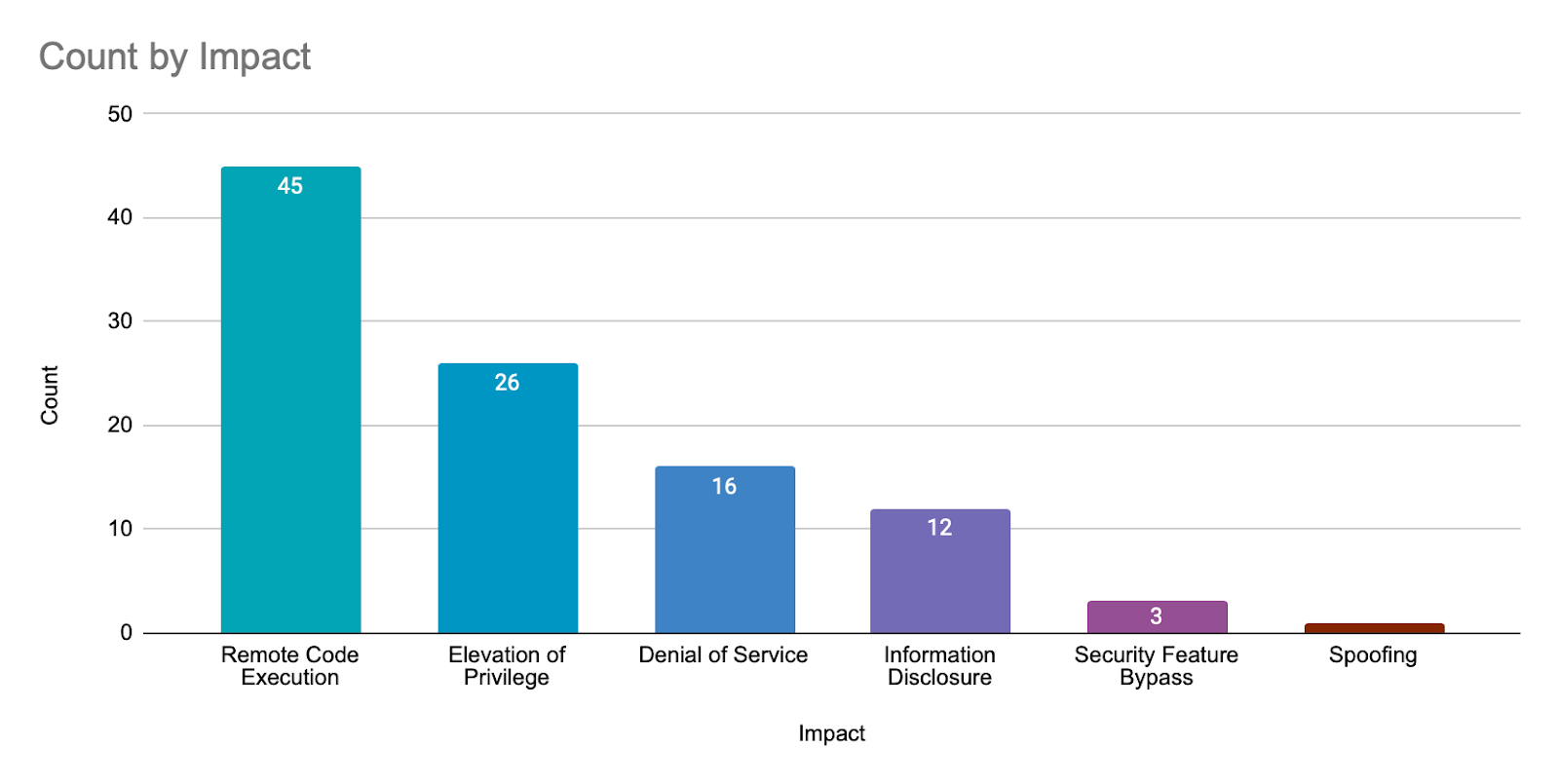
Kindly check the information gathered about October security updates :
|
CVEs |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Microsoft’s October 2023 Patch Tuesday, with security updates for 104 flaws, including three actively exploited zero-day vulnerabilities. While 54 remote code execution (RCE) bugs were fixed, Microsoft only rated twelve vulnerabilities as ‘Critical,’ all of which are RCE flaws..
Zero-day vulnerabilities: CVE-2023-41763 – Skype for Business Elevation of Privilege Vulnerability CVE-2023-36563 – Microsoft WordPad Information Disclosure Vulnerability CVE-2023-44487 – HTTP/2 Rapid Reset Attack Microsoft says that the CVE-2023-41763 and CVE-2023-36563 were publicly disclosed.
Windows Server 2016 has 28 CVEs: 12 Critical and 74 Important Critical CVEs :
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
KBs for Windows Servers 2016 |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
1- KB5030504 (Sep-Servicing stack update) 2- KB5030213 (Monthly Security Update) 3- KB5031362 (Monthly Security Update) |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Exchange 2016 Security Updates |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
KB5025903 |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
**** in this month recommended to install 4 Security Updates :
KB5030504 (Sep.-Servicing stack update, if not installed )
KB5030213 Oct-security update to mitigate the below CVEs,
KB5031362 security update to mitigate the below CVEs,
- KB5030504 (Servicing stack update)
Before installing Security updates:
Microsoft strongly recommends you install the latest servicing stack update (SSU) for your operating system before installing the latest cumulative update (LCU). SSUs improve the reliability of the update process to mitigate potential issues while installing the LCU and applying Microsoft security updates.
the latest SSU (KB5030504) as mentioned …
- 2- KB5030213 (Monthly security update Windows Server 2016):
Highlights:
- This update addresses security issues for your Windows operating system.
Improvements:
This security update includes quality improvements. When you install this KB:
- This update supports daylight saving time (DST) changes in Israel.
- This update addresses an issue that affects remote procedure calls (RPC) to the Win32_User or Win32_Group WMI class. The domain member that runs the RPC contacts the primary domain controller (PDC). When multiple RPCs occur at the same time on many domain members, this might overwhelm the PDC.
- This update addresses an issue that affects the LanmanServer Service. It stops working in clusters that do not have an Administrative Access Point. These are also known as AD-Detached Clusters. They are recommended for Microsoft Exchange on some versions of Windows. To learn more, see Database availability groups.
- This update addresses an issue that affects authentication. Using a smart card to join or rejoin a computer to an Active Directory domain might fail. This occurs after you install Windows updates dated October 2022 or later. For more details, see KB5020276.
Known issues in this update :
Microsoft is not currently aware of any issues with this update.
2- KB5031362 (Monthly security update Windows Server 2016) :
Highlights
- This update supports daylight saving time (DST) changes in Greenland.
- This update addresses security issues for your Windows operating system.
Improvements
This security update includes quality improvements. When you install this KB:
- New! IE mode and Microsoft Edge can now share cookies. To learn more, see Cookie sharing between Microsoft Edge and Internet Explorer.
- New! This update completes the work to comply with the GB18030-2022 requirements. It removes and remaps characters for Microsoft Wubi input and Microsoft Pinyin U-mode input. You can no longer enter character codepoints that are not supported. All the required codepoints are up to date.
- This update changes the spelling of Ukraine’s capital from Kiev to Kyiv.
- This update addresses an issue that affects external binding. It fails. This occurs after you install Windows updates dated May 2023 or later. Because of this, there are issues that affect LDAP queries and authentication.
- To protect against CVE-2023-44487, you should install the latest Windows update. Based on your use case, you can also set the limit of the RST_STREAMS per minute using the new registry key in this update.
|
Registry key |
Default value |
Valid value range |
Registry key function |
|
Http2MaxClientResetsPerMinute |
500 |
0–65535 |
Sets the allowed number of resets (RST_STREAMS) per minute for a connection. When you reach this limit, the connection ends. |
If you installed earlier updates, only the new updates contained in this package will be downloaded and installed on your device.
3- KB5030877 Exchange 2016 CU23 Security Updates:
CVE-2023-36778 —à to mitigate this CVE you must be install Exchange August Security update KB5030524 |
his security update rollup resolves vulnerabilities in Microsoft Exchange Server. To learn more about these vulnerabilities, see the following Common Vulnerabilities and Exposures (CVE):
Issues that are fixed in this update
- Extended Protection causes Outlook for Mac not to update the OAB
- Details Templates Editor fails and returns BlockedDeserializeTypeException
- Users in account forest can’t change expired password in OWA in multi-forest Exchange deployments after installing August 2023 SU
It’s required to Enabling Extended Protection in Exchange Server:
To enable Extended Protection on Exchange-based servers, see Extended Protection enabled in Exchange Server (KB5017260).
Known issues with this release
There are no known issues with this update.
Issues resolved in this release (see KB for full list)
Users in account forest can’t change expired password in OWA in multi-forest Exchange deployments af… (please note that additional steps are necessary)
Extended Protection causes Outlook for Mac to fail to download the OAB (we are releasing the new version of the Extended Protection script)
-àKB5030877 + KB5031362 OS Security Update
CVE-2023-21709 now has a better solution: install update for CVE-2023-36434
During the release of August 2023 SUs, we recommended to use a manual or scripted solution and disable the IIS Token Cache module as a way of addressing CVE-2023-21709. Today, Windows team has released the IIS fix for root cause of this vulnerability, in the form of fix for CVE-2023-36434. We recommend installing the IIS fix after which you can re-enable Token Cache module on your Exchange servers.
If you did not do anything to address CVE-2023-21709 yet:
Install update for CVE-2023-36434 on all your Exchange Servers.
If you have followed our August 2023 recommendation and disabled the Token Cache module (either by using single-line command or our CVE-2023-21709.ps1 script), or want to address possible performance concerns you have seen since disabling the module, do the following:
Install update for CVE-2023-36434 on all your Exchange Servers.
Re-enable IIS Token Cache module by doing one of the following:
To enable Token Cache module on individual server only, run the following from the elevated PowerShell window:
New-WebGlobalModule -Name “TokenCacheModule” -Image “%windir%System32inetsrvcachtokn.dll”
To enable Token Cache module on all servers in the organization (after Windows Updates were installed), you can use our CVE-2023-21709.ps1 as Administrator in Exchange Management Shell (EMS):
.CVE-2023-21709.ps1 -Rollback
Best Regards,
Hazem Mohamed
E-Mail: hmohamed200@gmail.com


